Learn more about what continuous penetration testing is, the types of continuous penetration testing and how your organisation can benefit.
Why is Penetration Testing Important?
Penetration testing – or pen testing, pen test, etc – is used to evaluate any organisation’s security vulnerabilities that an attacker might use for exploitation. Pen testing can be conducted on internal and external infrastructure, any IT systems or web applications which a company uses as part of their business operations.
Penetration testing is used to identify potential threats, such as:
- Where a hacker might attack
- How threat actors would gain access to your systems
- How strong your current security posture is
- How effective current defences are
- The potential impact of a serious cyber breach


Insights provided by pen test reports should inform as to what updates are needed to address vulnerabilities, but also what changes should be made to the company’s security policies.
However, pen tests can only offer a snapshot of vulnerabilities found at the time of testing or vulnerability scanning. With frequent software updates and application and system changes being deployed regularly, it’s best to conduct a penetration test whenever these upgrades take place.
Any weaknesses created by an upgrade would go unaddressed if the next pen test was still months or even a year away.
CREST recommend that pen testing is carried out at least annually. After all, threat actors aren’t waiting patiently to attack only one day a year. IT and business leaders recognise that more regular pen testing will ensure that their business is safeguarded against security vulnerabilities on an ongoing basis.
This is known in the industry as continuous penetration testing.
What is Continuous Penetration Testing?
The proliferation of digital transformation and new tools and technology poses a serious security challenge for businesses. Testing for weaknesses and vulnerabilities just once a year is no longer sufficient to protect the organisation.
While these annual, or half year or quarterly, tests can provide a snapshot of a company’s potential vulnerabilities, in isolation they can’t paint an accurate picture. It’s imperative that continuous penetration testing is conducted to protect networks, applications and systems.
Continuous penetration testing – also known as continuous security testing – will enable you to safeguard your security posture on an ongoing basis before a cybercriminal has a chance to exploit your vulnerabilities.
Learn More

Continuous penetration testing is a series of pen tests, following a full penetration test. While the full test presents a baseline, continuous penetration testing is triggered when any changes to the network, system or application happens from that base point.
Alongside the baseline annual penetration testing, managed penetration testing on a continuous basis eliminates any new weaknesses that could be exploited.
The cycle of continuous penetration testing should start from the baseline managed cyber penetration test.
The process should then include steps which define the scope and assets to be continuously tested, a schedule of regular security testing, remediation of any issues identified, retesting and ongoing tracking of upgrades, misconfigurations and newly reported threats and vulnerabilities.
Malicious cyberattacks are happening all hours of the day and night globally. Continuous penetration testing is a more realistic and effective method to keep a business secure in the modern day.
92%
of network perimeters are breached during penetration testing

16%
of penetration testing found evidence of earlier breaches
2m
A security breach can cost a business over £2M
The Main Types of Penetration Testing
As technology advances and the methods that cybercriminals use to gain access to networks, systems, and applications get increasingly creative, so do the types of penetration testing.
Defining the needs and targets of your continuous penetration testing as part of a full scoping exercise is essential to prevent malicious third parties from breaching systems and stealing valuable information and data.
There are three common types of penetration testing. The goal of any of these test types is the same – to attempt to gain access to an organisation’s networks, systems or applications using the same methods as a hacker might in order to exploit vulnerabilities.
Black Box Testing
This method examines functionality with no prior knowledge of the system, application or infrastructure being tested.
White Box Testing
This cyber security testing method looks at the internal source coding structure aided by full information disclosure on the target.
Grey Box Testing
This method is similar to white box testing but with only limited knowledge of the system, application or environment being targeted.
There are a range of common penetration testing services to consider when looking to test flaws in web application security, internal or external networks and IT systems.
There are also specific penetration testing services for PCI DSS compliance, social engineering and full red team assessments to test people and processes. These are mainly dependent on business needs and industry regulations.
Web application penetration testing will check the functionality of websites to pinpoint any failings or weaknesses. Continuous web application penetration testing will defend against every conceivable online threat.
Regular mobile application penetration testing will look for a range of exploitable vulnerabilities that cybercriminals may take advantage of.
With continuous penetration testing of internal environments, systems and procedures, businesses can ensure they have all the right countermeasures in place to prevent unauthorised access to privileged information.
Internal network penetration testing is designed to simulate cyberattacks from within the organisation, highlighting potential issues and guarding against threats from malicious insiders.
Continuous external penetration testing can identify any gaps in external network infrastructure to allow the necessary remediations.
On completion of external network penetration testing any security flaws can be addressed, eliminating potential threats before they can cause damage.
Discuss your cyber security options
Get in touch today to speak to an expert and secure your business, or call us on 0800 090 3734
The Steps in Continuous Penetration Testing
Managed cyber penetration testing assistance typically goes through 5-6 phases. If any provider offers fewer steps than this, be aware that they may be offering a far inferior continous penetration testing service than is available elsewhere.
The Benefits of Continuous Penetration Testing
Why consider continuous penetration testing for your company?
By conducting continuous penetration testing, any organisation can ensure that their networks, applications and systems are fully protected from cyber threats.
With continuous penetration testing, businesses can maintain a strong security posture all year round. In a world where hacking techniques proliferate, so must traditional penetration testing.

The tactics, techniques and procedures (TTPs) that hackers use to attack business systems are growing in volume and sophistication. By investing in continuous penetration testing, not only can businesses safeguard their cyber security before a cybercriminal has a chance to exploit vulnerabilities – they can also improve internal security management processes.
This will remove time constraints around annual testing, allow for a deeper and wider variety of penetration testing to be done, and protect the organisation more effectively against cyber attacks.
The insight that continuous penetration testing can provide organisations with a clear picture of their attack surface and risk profile. If any gaps are left unpatched or unaddressed, bad actors are likely to exploit and compromise the business.
Continuous penetration testing ensures all necessary security controls and processes are in place, gaps are remediated and helps to reduce information security risk.
Without regular checks, the time to remediate issues shown by a pen test might extend to the next test a year later. Any weaknesses left unpatched are a huge risk to business operations and will be exploited by threat actors. Using continuous penetration testing to monitor weaknesses ensures that remediation actions are completed promptly and helps reduce information security risk.
Firstly, it’s not always possible for organisations to hire security professionals in-house, especially when considering the cyber security skills gap. The best way to support in-house teams is to outsource continuous penetration testing to a managed penetration testing provider.
These highly qualified pen testing teams bring industry-wide insight and extensive knowledge of the entire threatscape. Continuous penetration testing also improves budgeting by giving regular updates on where the most pertinent spend is needed.
According to a recent study, perceived ROI (return on investment) is dropping in over half of organisations due to the complexity of managing cybersecurity budgets. The same report states that security costs are creeping towards $3m annually, but only 51% rate these efforts as effective.
By identifying the areas that need urgent investment, cyber risk management is also improved providing a better and more immediate ROI.
There are specialised skills and qualifications needed to conduct continuous penetration testing. The cyber security industry is short of 2.7 million workers.
By outsourcing to a managed cyber penetration testing provider and having testers perform continuous security testing, businesses free internal staff to work on in-house projects. Read further on 3rd Party Penetration Testing.
20%
of tests find critical vulnerabilities
100%
of red team assessments found sensitive data begin transferred

4 days
is all It takes for a hacker to breach a network and gain access to data and systems
Discuss your cyber security options
Get in touch today to speak to an expert and secure your business, or call us on 0800 090 3734
Why choose DigitalXRAID’s continuous penetration testing services?
If you’re serious about security, move to a continuous penetration testing model.
DigitalXRAID’s managed cyber penetration testing assistance will provide continuous penetration testing to identify any weaknesses and vulnerabilities in your systems, networks and applications. We give you the chance to remedy issues before threat actors can exploit them, protecting you from attacks.
DigitalXRAID is one of the first managed penetration testing providers to gain CREST certification for our continuous penetration testing services. This makes us one of the top penetration testing providers in the world.
If there’s a vulnerability, DigitalXRAID’s penetration testing experts will find it.
For more information on our continuous penetration testing services and how we can support you in staying a step ahead of cyber criminals, speak to an expert.
For an in-depth view of what the continuous penetration testing service entails and to get tailored quote: scope your project.
DigitalXRAID has a unique insight into offensive security testing techniques. With cyber security services operating on the defensive side as well as offensive, we have a more holistic view, and a much deeper understanding of what techniques are being used for attack. Therefore, our continuous penetration testers will dive deeper, uncovering vulnerabilities that others tend to miss.
DigitalXRAID’s top qualified security testers can offer penetration testing services, including:
- Internal Penetration Testing Services
- External Penetration Testing Services
- PCI DSS Penetration Testing Services
- Red Teaming
- Social Engineering
- Mobile app Penetration Testing Services
- Web application Penetration Testing Services
- And many more
Our continuous Penetration Testing Services

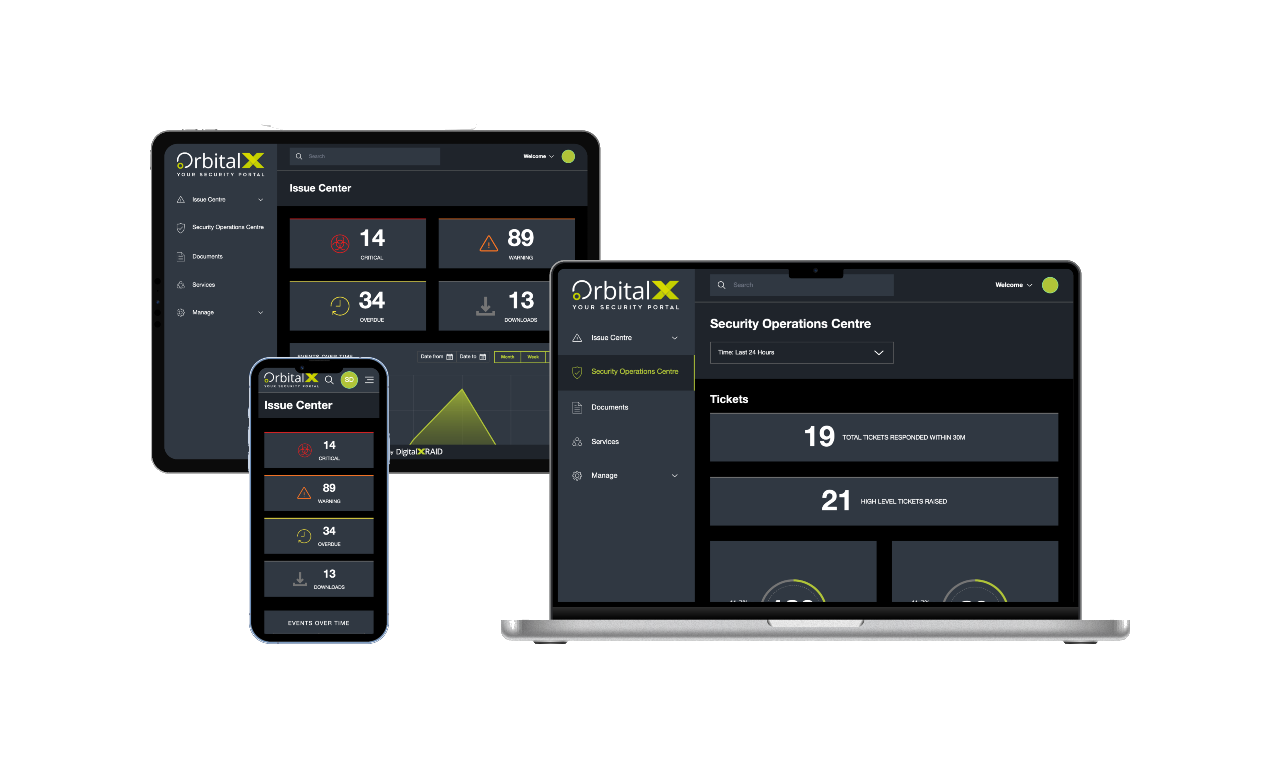
YOUR SECURITY PORTAL
Get full visibility of your cyber Security anytime, anywhere
OrbitalX – Your Security Portal
- Bridge the gap between vulnerability identification and issue remediation with timely, actionable insights
- Report the value of security programs to senior management with concise, specific reports, enhancing awareness and aiding in securing future budgets
- Build a comprehensive roadmap to full protection, incorporating defence in depth as your cyber security needs grow
Prevent Vulnerabilities
OrbitalX prevents vulnerabilities and other security issues from being overlooked, ensuring timely resolution and clear reporting on any missed issues or resource constraints.
Manage & Mitigate Risks Faster
- Gain greater visibility into your vulnerability status with your real-time vulnerability dashboard updates, categorised into Critical, High, Medium, and Low status.
- Prioritise and assign remediation tasks effortlessly based on the vulnerability type, ensuring prompt action and risk mitigation.
- Reduce your risk by tracking vulnerability resolution over time
Stay Ahead of Cyber Threat
- Take immediate action to remediate vulnerabilities before they can be exploited, keeping you one step ahead of hackers
- Communicate vulnerability status clearly across all business departments to ensure everyone is informed and risks are understood.
- Track and report vulnerability identification and remediation progress over time for a clear audit trail and live resolution status.
Enhanced Visibility
- OrbitalX provides enhanced visibility for a comprehensive view of your security and risk landscape
- Make informed business decisions based on real-time risk data to better protect your business from threats
- Move to a fully digital format for added value through linear granularity of your entire managed security service, with easy access to digital reports instead of cumbersome PDFs
Streamline Reporting
- Streamline cyber security reporting, moving away from outdated PDFs and emails to a dynamic, digital format.
- Quickly and accurately report on vulnerability resolution status, customising reports with relevant data for business stakeholders.
- Customise charts and diagrams for detailed and stakeholder-specific reporting.

Protect Your Business & Your Reputation.
With a continued focus on security, you can rest assured that breaches and exploits won't be holding you back.